Classical internet
vs Quantum internet
Why do we actually want to build a quantum internet?
Apart from the fact that the process teaches us new physics, will a quantum internet
have added value over the classical internet - the internet that we are currently all using?
What are the differences and similarities between the classical and quantum internet?
Classical internet
What is it?
If you send digital information over the classical internet, this information is built up of bits. A bit can take two values: we call them 0 or 1.
For example, we can send the following digital information from our computer to another computer by using the classical internet:
01001001
01101110
01110100
01100101
01110010
01101110
01100101
01110100
And while for us this looks like a random bunch of 0 and 1’s, a computer knows that, in a kind of encoding called ASCII, we’ve actually sent over a word - namely the word ‘Internet’.
Development
During the cold war, the US military feared that a Soviet attack could easily destroy the whole telephone network. If that would happen, long-distance communication would not be possible anymore. A scientist working for the Massachusetts Institute of Technology (MIT) as well as the U.S. Defense’s Advanced Research Projects Agency (DARPA) consequently developed a network between computers. This ARPANET would be less vulnerable to a Soviet attack than the telephone network. By connecting computers with cables, information could be sent from computer to computer. Furthermore, a method was developed that was able to break down information into smaller packets, so that each packet could take its own route between the computers. The very first attempt to send a message over the ARPANET – the word “LOGIN” – was undertaken in 1969.
Login
At the University of California at Los Angeles (UCLA), they typed an “L”. And in Stanford University an “L” appeared on the screen. Afterwards at UCLA the letter “O” was sent. In Stanford, they could now see “LO” on the screen. The third letter, “G”, crashed the system.
Quantum internet
What is it?
A quantum internet works with quantum bits – so called qubits. Qubits follow the rules of quantum mechanics.
Qubits cannot be measured without being disturbed. This is a big advantage for the security of the quantum internet, but at the same time forms a difficulty for communicating over larger distances because it makes it impossible to amplify or repeat the signal.
More information on qubits and their properties
Development
One of the goals of QuTech is to develop the technology to enable quantum communication between any two places on earth. The first step towards achieving this goal is building the first real quantum network between the cities of Delft, The Hague, Leiden and Amsterdam. This quantum network should be up and running in 2022 and can be seen as the quantum version of the ARPANET.

Once a quantum network is operational in the Netherlands, the next step is to extend it to Europe. The European Quantum Internet Alliance, an alliance of Europe’s quantum research institutes and actors from industry, works on a scalable design to make such a large-scale network possible.
Cryptography Classical Internet
Public key cryptography
Three decades after the first message had been sent over the ARPANET, the US National Institute of Standards and Technology (NIST) established an encryption standard called Advanced Encryption Standard (AES). This encryption standard (a type of symmetric encryption) is still used today, although much communication is currently secured via public key cryptography (asymmetric encryption).
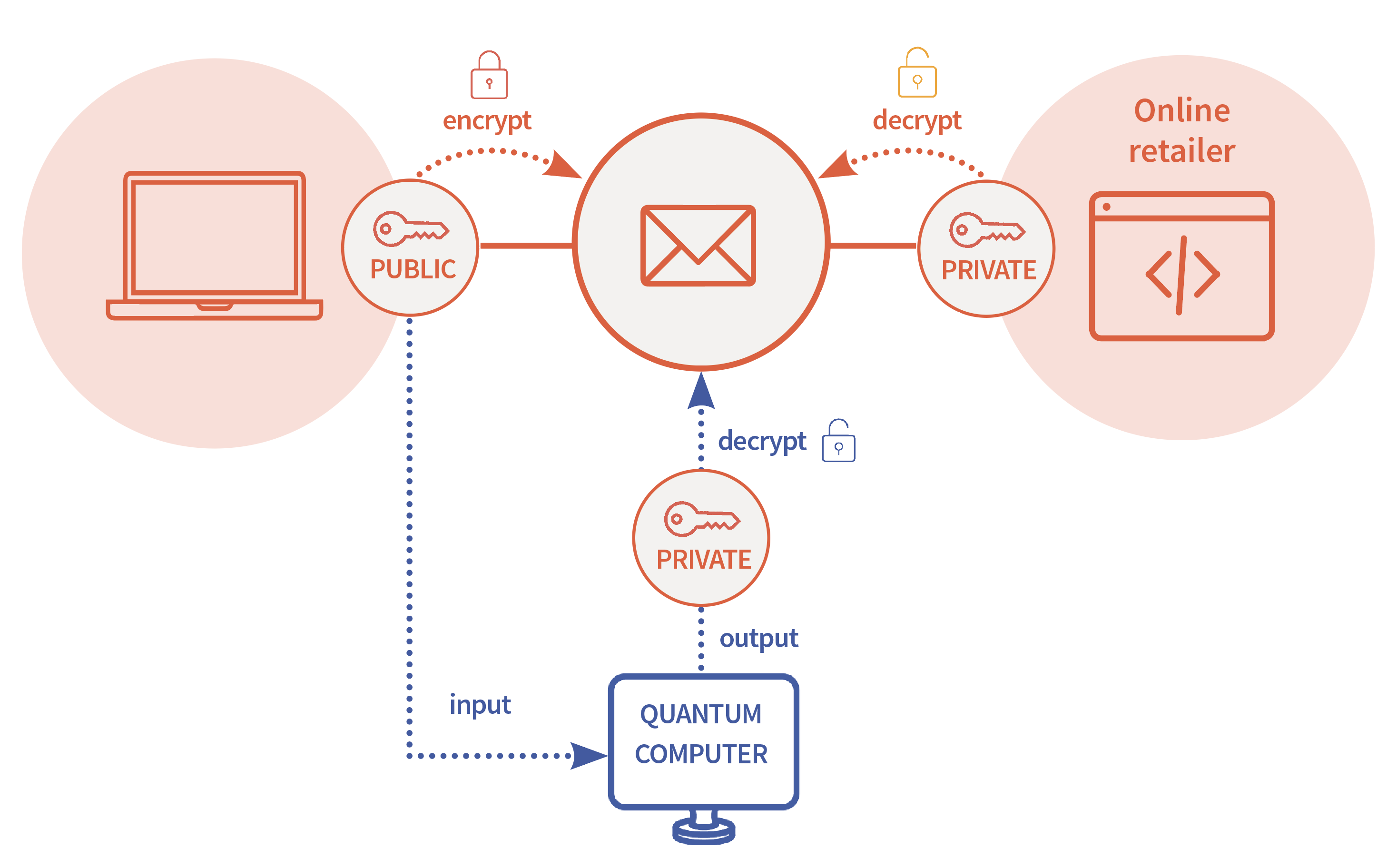
How does public key cryptography work?
If you buy something online, your communication with the online retailer is usually secured through public key cryptography. Public key cryptography works with a private key and a publicly available and freely shared key. You encode your message using the online retailer’s public key and the online retailer decrypts the message with their private key.
Safety
If the message happens to be intercepted along the way by an eavesdropper, it is extremely difficult for that person to decode the information in your message. Only if the eavesdropper can get their hands on the private key, they can break the encryption. In some cases, the eavesdropper can obtain the private key from the public key with a method called prime factorization. However, this is an extremely difficult problem: today’s most powerful supercomputer would take about a year to solve such a challenge. For all practical purposes, such encryption is unbreakable.
Still, the Canadian Global Risk Institute estimated that there is a ‘one in seven chance that some of the fundamental public-key cryptography tools upon which we rely today will be broken by 2026 and a 50% chance by 2031’. This can be caused by faster factoring algorithms, an increase in computing power or a large-scale quantum computer. A quantum computer should be able to do this, because it can find the prime factors of large numbers much faster than classical computers with the help of an algorithm developed by Peter Shor in 1994. Fortunately, large-scale quantum computers do not exist yet. But they are being developed, so a response is required. Two types of response are possible. One is to develop new encryption techniques that rely on information exchange over the classical internet; this is called classical post-quantum cryptography. The other involves using a quantum internet for creating encryption keys; this is called quantum key distribution.
Response 1

Classical post-quantum cryptography
Classical post-quantum cryptography, also referred to as quantum-proof or quantum-resistant cryptography, are techniques that are expected to be secure against attacks from quantum computers. One possible solution might be to use symmetric keys. Although a quantum computer running Grover’s algorithm can break such a symmetric key, increasing the key size is expected to make it quantum-resistant. Other examples of public key cryptosystems that are believed to be secure against quantum computers are lattice-based cryptography, hash-based cryptography, code-based cryptography, multi-variate cryptography and supersingular isogeny-based cryptography. Some organisations are already implementing these cryptosystems, even though standards for classical post-quantum cryptography have not been agreed yet.
Response 1

Quantum key distribution
In 1984, computer scientists Charles Bennett and Gilles Brassard invented a scheme to securely distribute a key with the use of quantum mechanics. Since then a lot of versions of this scheme have been developed, which are all known as quantum key distribution. In quantum key distribution, parties create an encryption key over a quantum network. For sending the encrypted communication the parties still use the classical internet. Since quantum key distribution does not depend on the factorization of large numbers in prime numbers, the encryption keys that quantum key distribution gives cannot be broken by the Shor algorithm running on a quantum computer or by other fast algorithms for prime factorization.
Cryptography Quantum Internet
How does quantum key distribution work?
In quantum key distribution usually single particles of light are used, called photons.
There are two types of quantum key distribution with such photons.
Type 1 - Preparation and read out
In type 1, a person A – let’s call her Alice – prepares photons in a certain state and sends them over the quantum internet to person B, called Bob. Bob measures the photons to determine their prepared state. In this way Alice and Bob exchange a key.


Safety type 1
This key exchange is safe. If an eavesdropper, let’s call her Eve, wants to get her hands on the key, she needs to measure the photons that Alice sends to Bob. However, by measuring a photon, the state of the photon changes, and this change is something that Alice and Bob can detect. So Alice and Bob can check if Eve has listened in during the exchange of a key, and thus determine if the key is compromised. Compromised keys are thrown away; Alice and Bob only keep keys created in exchanges where no eavesdroppers were detected.

Type 2 - Device independent, entanglement-based
Type 2 is based on entanglement. Alice and Bob each have a qubit. They then establish entanglement between their qubits, using photons that they send over a quantum network. A key can be distributed between Alice and Bob using this entanglement between their qubits. Alice and Bob do this by both performing measurements on their qubits, and sharing (through a link over the classical internet) information about these measurements.


Safety type 2
This scheme is also safe. If Eve tries to eavesdrop, she will reduce the amount of entanglement between the qubits of Alice and Bob. And Alice and Bob can again detect this, and thus determine if the exchanged key is compromised.
Moreover, it turns out that entanglement allows the scheme to be safe even if the devices that Alice and Bob use to distribute the keys have been maliciously prepared by Eve. Such schemes are called device independent.

References
www.dictionary.com/browse/internet
www.unit-conversion.info/texttools/convert-text-to-binary/
www.history.com/topics/inventions/invention-of-the-internet
Kaliski, B.
The Mathematics of the RSA Public-Key
Cryptosystem. RSA Laboratories.
Mosca, M. (2016).
A quantum of prevention for our cyber-security. Institute for Quantum
Computing & Special Advisor on Cyber Security to the Global Risk Institute, Toronto
NIST. (2017). Post-Quantum Cryptography. Project Overview.
